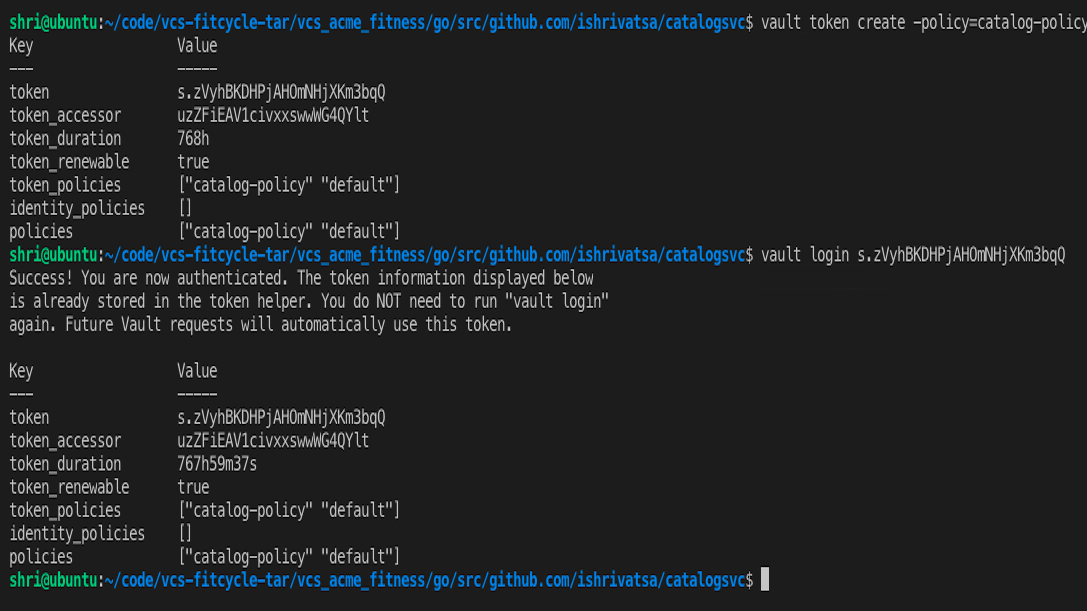
Trusting your ingredients - What's in your function anyway?
Whether you're building apps or baking cheesecake, trusting the ingredients you work with and making sure you have a transparent process to get them into your final product is one of the most important things.
Continue Reading